
Vulnerabiliy Validation
At Global Telco scale
Top 5 Global Telco Licenses Reveald’s Epiphany Validation Engine

Top 5 Global Telco Licenses Reveald’s Epiphany Validation Engine
The global telco, one of the largest telecomunications providers in the world, provides telecommunications products and services. It provides traditional fixed-line service, Wi-Fi networks, data, hosted services , and IT services. With over 50,000 employees, the company also owns TV networks and has acquired—and runs—several telecommunications, cable TV, Internet, and Wi-Fi network companies is over 20 countries.
The global telco sought a robust cybersecurity solution to enhance its security posture. The company wanted to proactively protect its sensitive data from cyber attacks rather than respond to attacks after they occur.
After evaluating various options, the global telco decided to license Reveald’s Epiphany Validation Engine. They were drawn by its unique features and capabilities.
The global telco was impressed with a number of key aspects:
At the network architecture level, the Epiphany Validation Engine is installed as an Amazon Web Services (AWS) instance on the cloud. It is given access to an agent within an organization that holds all security controls—the golden image. Highlights of the platform are described below.
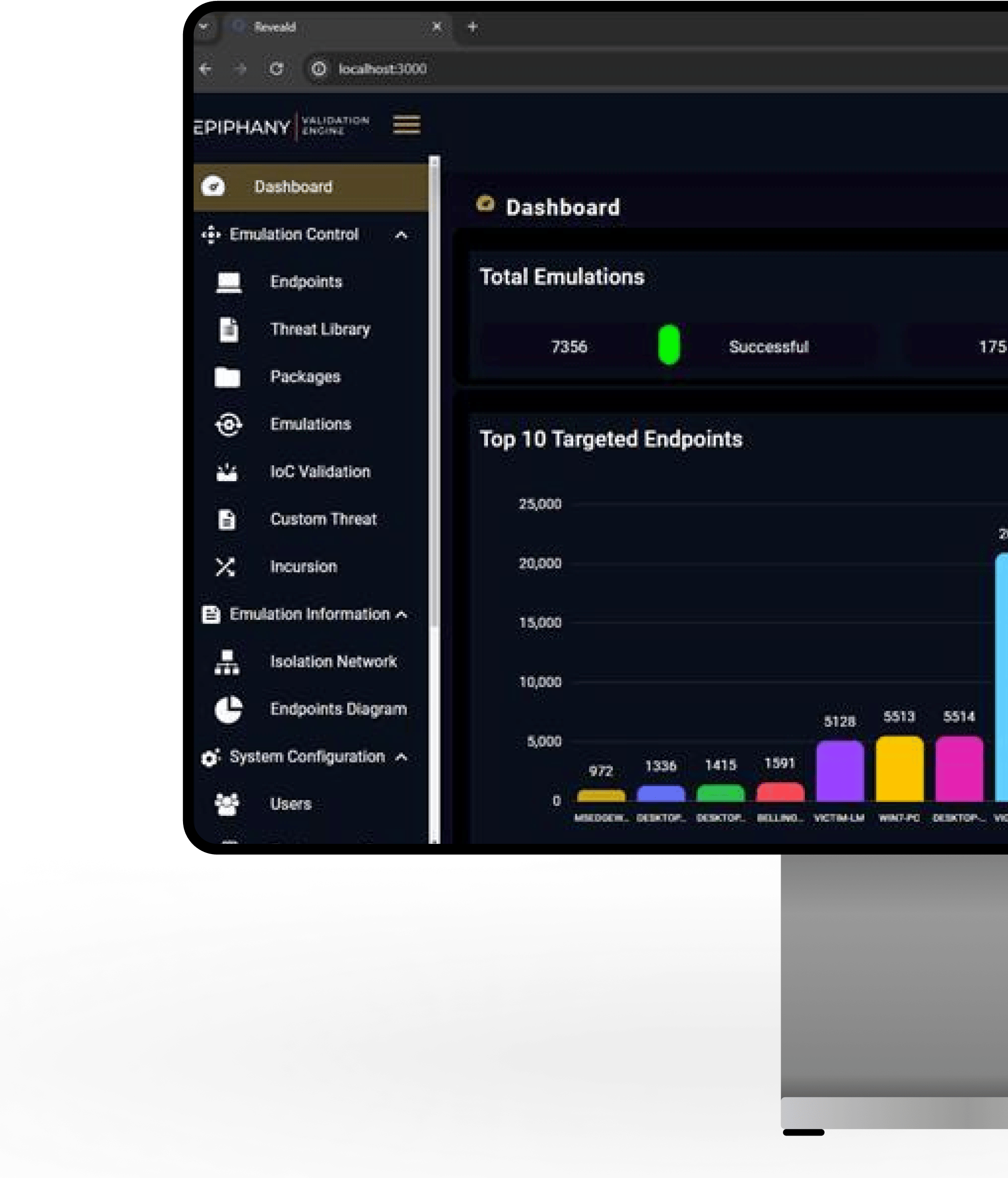
As a result of the deal inked between Reveald and the global telco, the Epiphany Validation Engine is driving various use cases for the organization, aligning with their security objectives:
As a result of the deal inked between Reveald and the global telco, the Epiphany Validation Engine is driving various use cases for the organization, aligning with their security objectives:
Let us know what your needs are for measuring and evaluating your company’s cybersecurity solutions.
Contact Us