
Welcome to the World of Cyber Threat Exposure Management
Master the attacker’s perspective – reduce business risk.
Navigating the future of predictive cybersecurity
What is Cyber Threat Exposure Management (CTEM)?
Continuous Threat Exposure Management (CTEM) is a cybersecurity approach aimed at predicting and prioritizing future threats. CTEM is not just technology; it’s a program that involves the continuous assessment of threat exposures combined with asset context and threat intelligence and uses advanced analytical methods to prioritize remediation. This approach, leveraging AI-driven platforms like the Reveald Epiphany Intelligence Platform, transitions organizations from reactive to predictive cyber defense.
“By 2026, organizations prioritizing their security investments based on a continuous exposure management program will be three times less likely to suffer from a breach.”
Gartner, 21 July 2022
Implement a Continuous Threat Exposure Management (CTEM) Program)
I Already Have a Vulnerability Management Program, do I Need CTEM?
Vulnerability Management (VM) is a core component of CTEM, but CTEM programs offer a broader scope that solves many of the challenges that organizations face with VM, such as:

Vulnerability Fatigue
VM solutions collect and report on tens of thousands of vulnerabilities, burying security teams in far more data than they can ever act upon.

Poor Prioritization
VM solutions tend to have static prioritization models, which fail to take into account the real and dynamic risk associated with vulnerabilities, and the potential for business impact.
Poor Business Alignment
Many organizations struggle to align vulnerability reports with business units and asset criticality, creating patchwork approaches to remediation.
Benefts of implementing CTEM
The implementation of Continuous Threat Exposure Management (CTEM) brings enormous benefits to an organization's overall cybersecurity program, including:


CTEM Turns effort into outcomes
Rather than simply chipping away at endless mountains of vulnerabilities, CTEM helps you prioritize and measure efforts in terms of reduced business risk.
By implementing a CTEM program, organizations are continuously aware of where they are exposed, and the best actions they can take to reduce that exposure.
THE 5 PHASES OF CTEM





Scoping
This initial phase involves identifying and understanding the organization's attack surfaces, determining what is critical to the business, and defining the scope of the CTEM program.
Discovery
This phase focuses on uncovering assets, identities, and resources, and evaluating their risk profiles. It involves enumerating permissions for users and services, identifying vulnerabilities and misconfigurations, and other security weaknesses.
Prioritization
In this phase, the program identifies the most significant risks and prioritizes them for remediation. This requires evaluating threats based on their impact, likelihood of occurrence, and their potential to affect critical business processes.
Validation
This phase focuses on uncovering assets, identities, and resources, and evaluating their risk profiles. It involves enumerating permissions for users and services, identifying vulnerabilities and misconfigurations, and other security weaknesses.
Mobilization
This phase focuses on making changes to the environment to mitigate risk - patching vulnerabilities, addressing IAM misconfigurations, resolving control configurations etc. Mobilizing the many teams and stakeholders to effectively mitigate risks.
In order to accomplish these phases, Gartner suggests organizations need a number of core capabilities that make up an effective CTEM program:


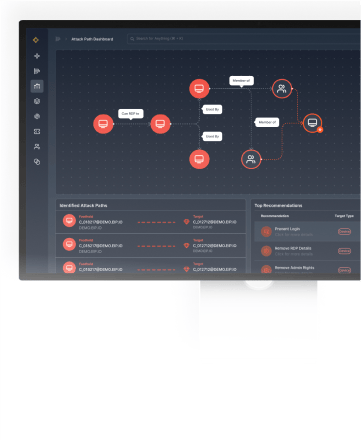
Challenges and Considerations in CTEM
It’s important to also consider the challenges and key considerations that organizations face when implementing a CTEM program. Despite its advantages, CTEM presents specific hurdles that need careful management and strategic planning.



Reveald Offers a Clear Path to Predictive Cybersecurity
Reveald is leading the way toward next-generation cyber defense by transitioning organizations from reactive to predictive strategies with our AI-powered Epiphany Intelligence Platform. Reveald’s unique combination of technology platform coupled with expert managed services is helping our customers to get off the vulnerability management treadmill and start reducing material risk across their organization.

