
Use Case: Moving to
Continuous Threat Exposure Management (CTEM)
Epiphany revolutionizes cybersecurity with Gartner's CTEM framework in the rapidly evolving digital realm.

Epiphany revolutionizes cybersecurity with Gartner's CTEM framework in the rapidly evolving digital realm.
In the rapidly evolving digital realm, staying ahead of cyber threats is not just about defense — it’s about anticipation and agility and embodying each step of Gartner’s Continuous Threat Exposure Management (CTEM) lifecycle is one framework which can help you achieve results.
Gartner - How to manage cybersecurity ThreatsIn the initial phase of the Cyber Threat and Exposure Management (CTEM) framework, known as Scoping, the primary objective is to meticulously delineate and comprehend the entirety of your digital ecosystem. This process involves the comprehensive cataloging of all digital assets, ranging from hardware components to software applications and network infrastructure.
The significance of this phase cannot be overstated, as it serves as the foundation upon which effective threat mitigation strategies are built. By conducting a thorough and exhaustive scoping exercise, organizations can unveil any concealed avenues of exposure that might otherwise remain unnoticed.
The depth and accuracy of the scoping effort directly correlate with an organization's ability to mitigate risks effectively. A comprehensive scoping endeavor provides invaluable insights into the intricate interdependencies within the digital landscape, enabling proactive identification and remediation of potential vulnerabilities.
The Epiphany Intelligence Platform, by seamlessly integrating with various solutions and leveraging its proprietary asset discovery technology, has the capability to compile a thorough inventory of assets for in-depth analysis.
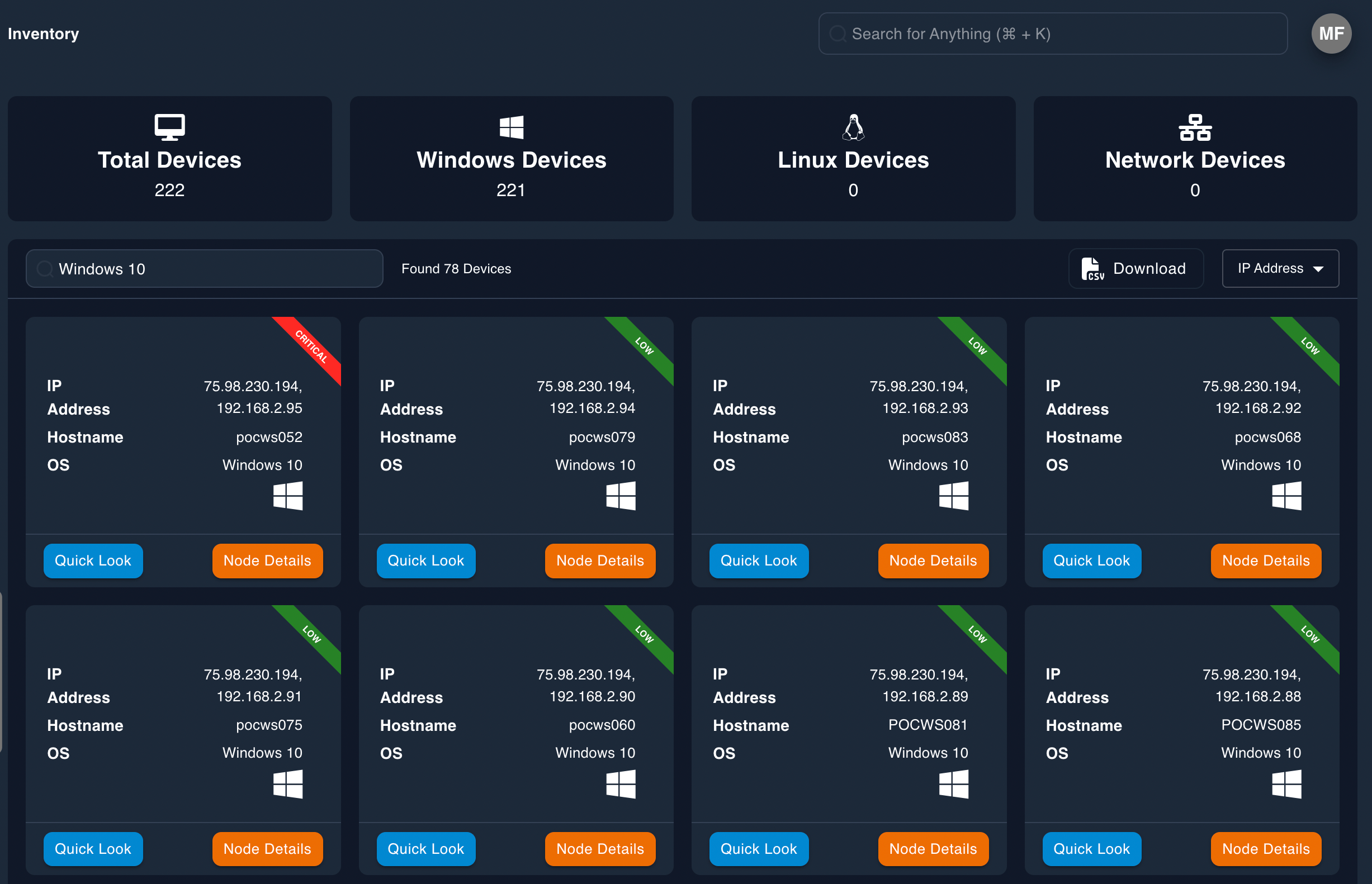
Asset Inventory
With the digital landscape scoped, the next step is to analyze each device and every opportunity for exposure and business risk. This is normally an exhaustive effort and relies on the expertise and knowledge of Red Team researchers to perform properly. Epiphany supports these experts by analyzing the digital environment and searching for 'footholds' which would allow an attacker to traverse through misconfigurations, vulnerabilities, and identity issues to a 'prize' - something which would cause material business risk.
By leveraging cutting-edge AI, Epiphany uncovers the unseen, bringing to light the weak spots that could be exploited by potential adversaries.
Using Epiphany’s connectivity into identity and access management (IAM) solutions, scanners, endpoint detection and response (EDR), and clouds, Epiphany can quickly highlight misconfigured systems in dark parts of your enterprise.
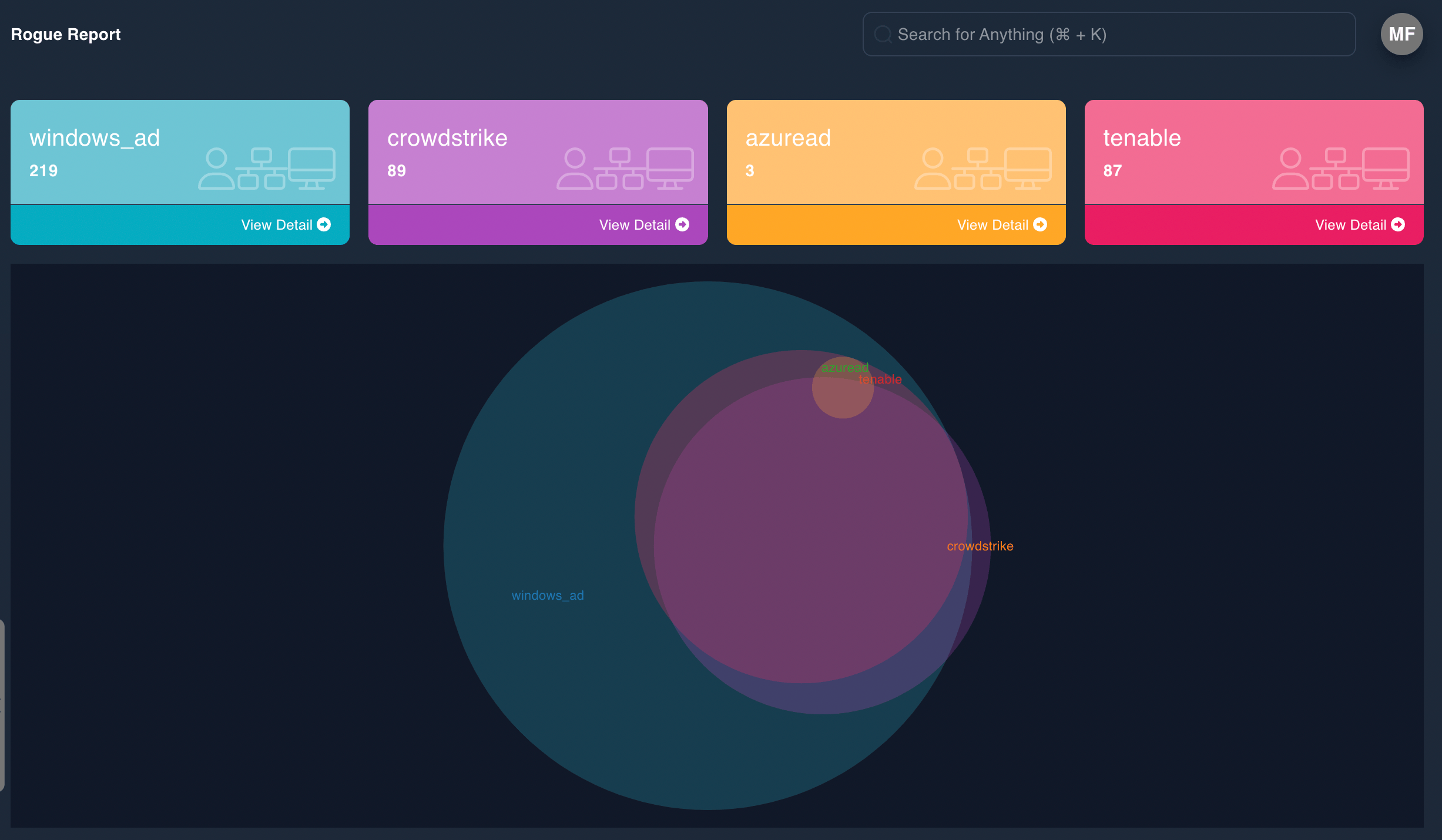
Configuration Assurance
In the prioritization phase, vulnerabilities, misconfigurations, patches and other exploitable issues are triaged to evaluate what to fix first. This prioritization evaluates business impact and risk to ensure the most likely, damaging issues are resolved or mitigated using the most appropriate measures. Not every flaw needs to be resolved, especially if there are mitigations or it poses minimal business risk.
Epiphany’s AI-driven analytics help achieve this prioritization by ranking problems based on their potential impact on your business operations and guides you to allocate your resources judiciously.
Understanding not just the individual assets that could be impacted but the whole asset catalog, Epiphany ensures you don’t miss where material impact may live. With Epiphany, your security efforts move from responsive to strategic.
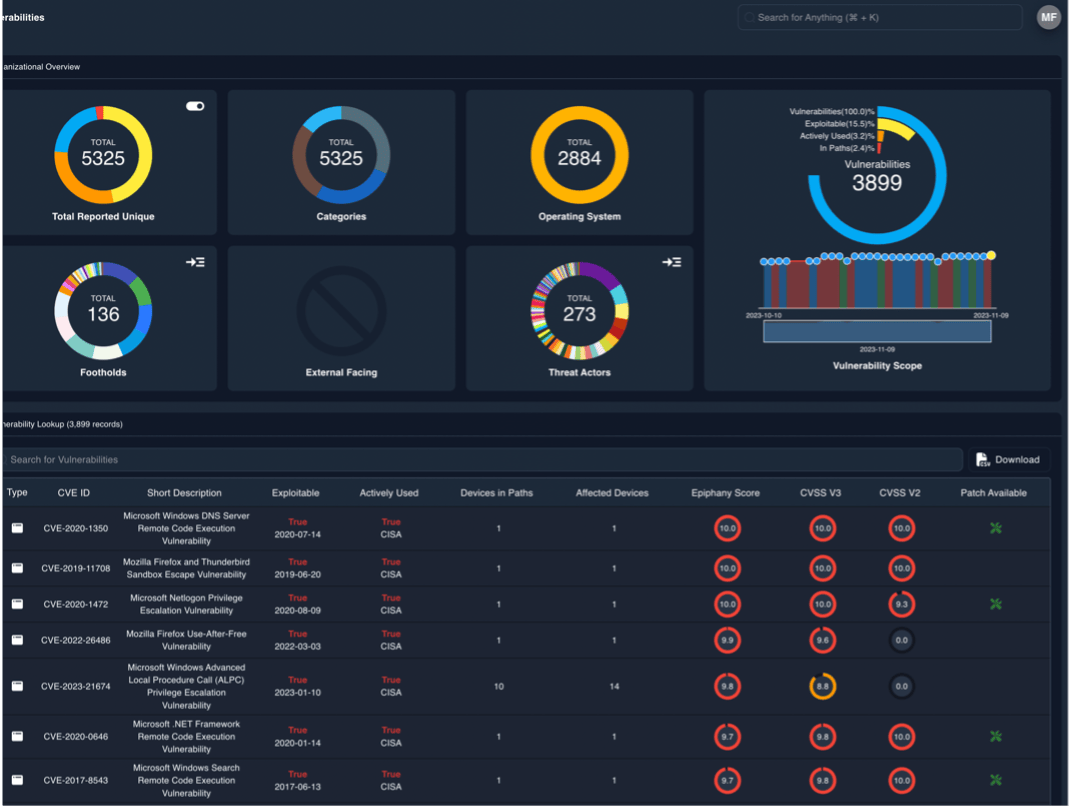
Vulnerability Prioritization
Before taking action, it's important to validate that the prioritized list of changes are both necessary and will be effective. Validating that controls and changes will create an effective reduction in risk is vital to ensure a continuous reduction in the business risk. The CTEM validation phase ensures that your efforts result in an improved risk posture. Epiphany understands this, which is why its validation phase is pivotal. Epiphany validates in three different ways:
Epiphany can evaluate, simulate, and emulate attack scenarios, test defenses, and validate security measures, ensuring that the shields you raise are not just present but validated to achieve the resulting mitigation of risk.
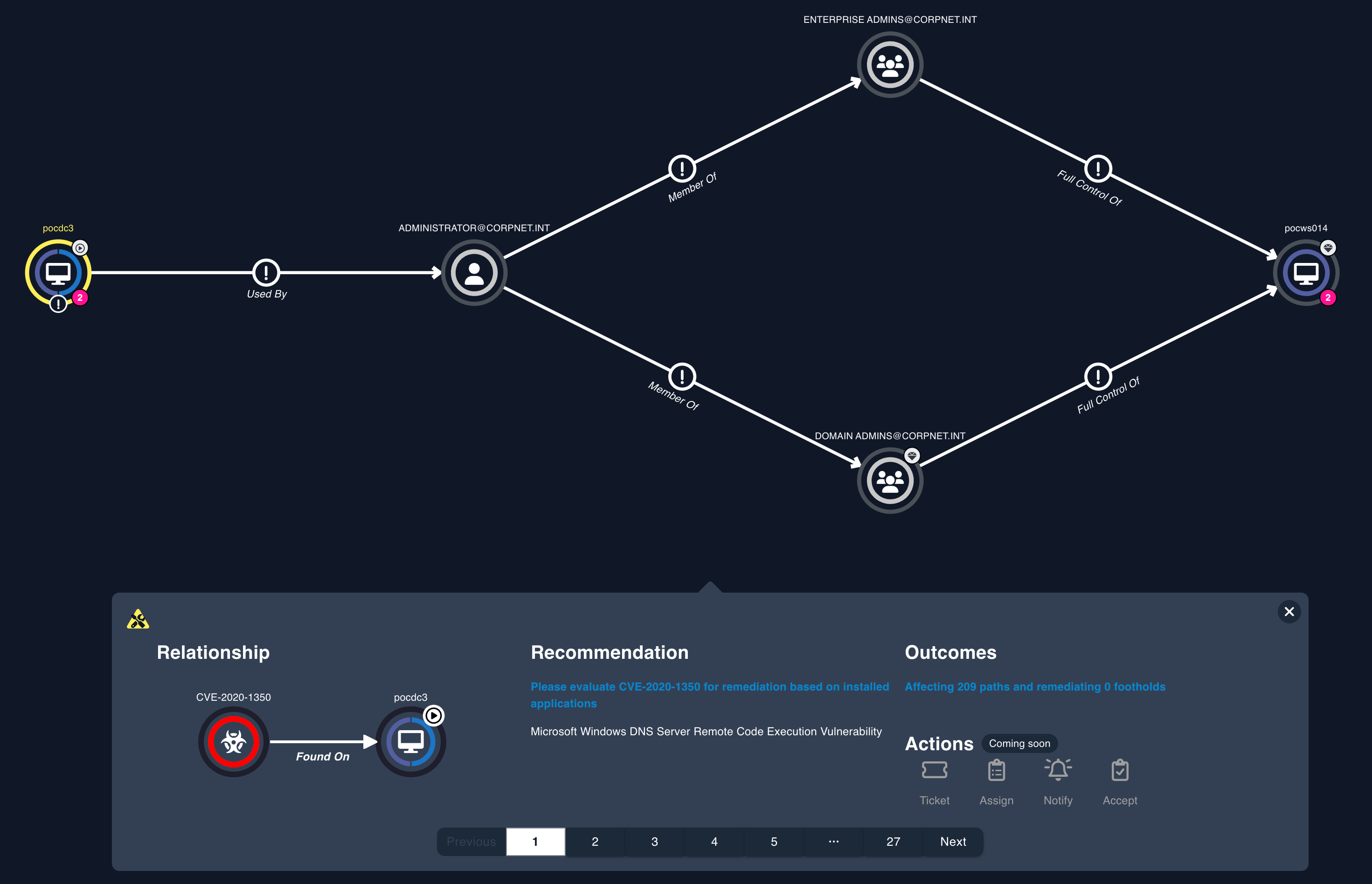
Attack Path Exploration
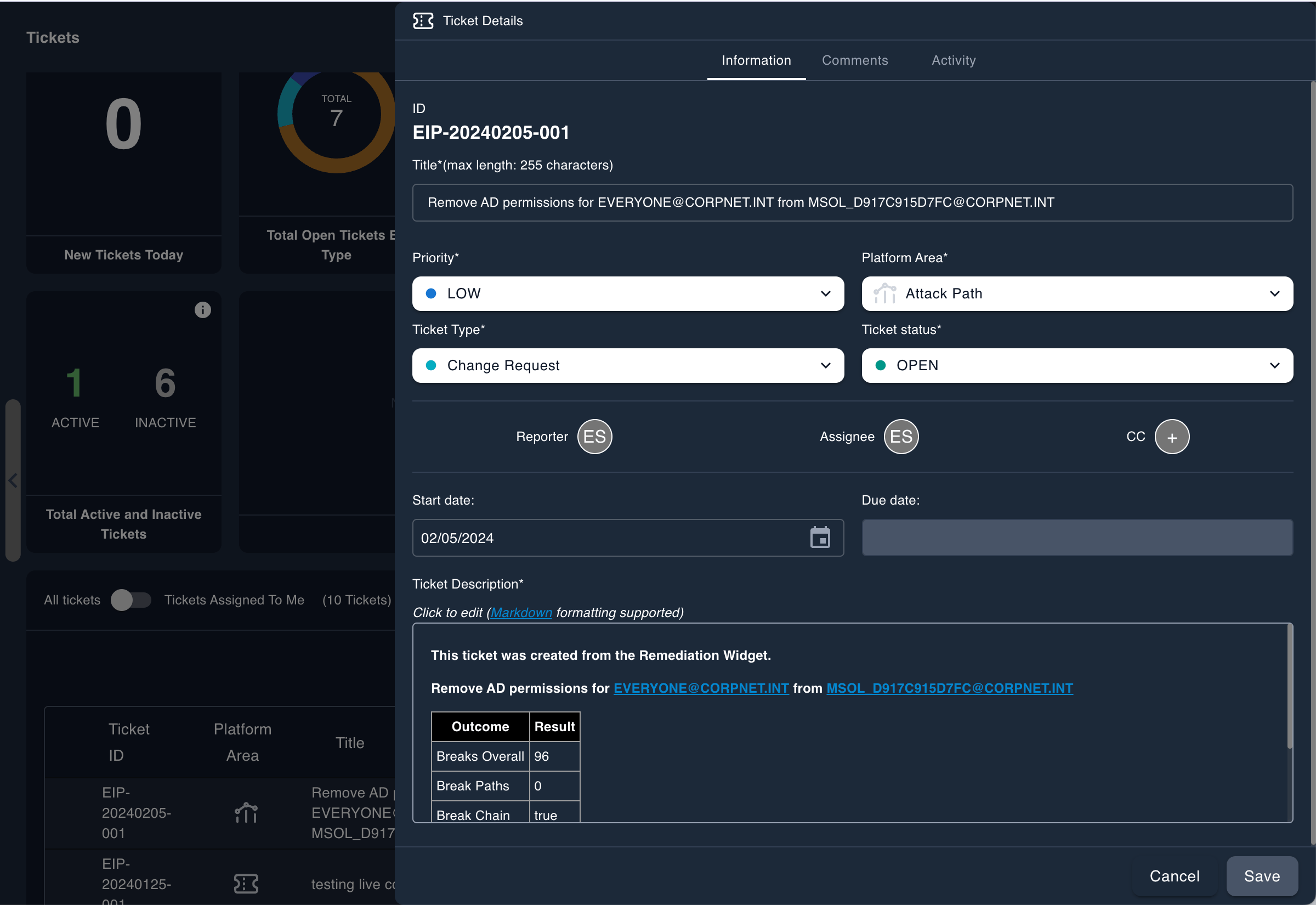
The final stage of CTEM, mobilization, involves action—mitigating the prioritized, validated items to improve the risk posture of the organization. Epiphany embodies mobilization, arming you with the tools and insights to act decisively. It streamlines coordination response with automation, ensuring that when an exposure is detected, the response is immediate, effective, and trackable.
Through integration with ticketing platforms and robust evidence collection and threat actor biographies, Epiphany collates all the information needed to effect a positive change.
Epiphany doesn’t just alert—it empowers action.
Outcome Tracking
The “C” in CTEM is important. CTEM is continuous—not a one-time exercise. A CTEM program is a regular cycle that repeats the five core steps that form the foundation of CTEM. Repetition of this process is key to ensure your threat exposure management program is effective and consistent.
Reveald combines decades of cybersecurity experience with leading technology and techiques, allowing customers to shift to predictive security instead of chasing ghosts.