

Leverage the power of AI to discover and prioritize cybersecurity risks, vulnerabilities and misconfigurations across your entire environment.
Get a DemoLearn More

Leverage the power of AI to discover and prioritize cybersecurity risks, vulnerabilities and misconfigurations across your entire environment.
Get a DemoLearn More
Sophisticated AI helps to Identify, prioritize, and eliminate exposures before adversaries can find and exploit them.

Closing security gaps reduces the day-to-day noise associated with predictable threats, creating dramatic reductions in downstream workloads.

Built on the Epiphany Intelligence Platform, with simple integrations to common IT infrastructure, you’ll see results in a matter of days.
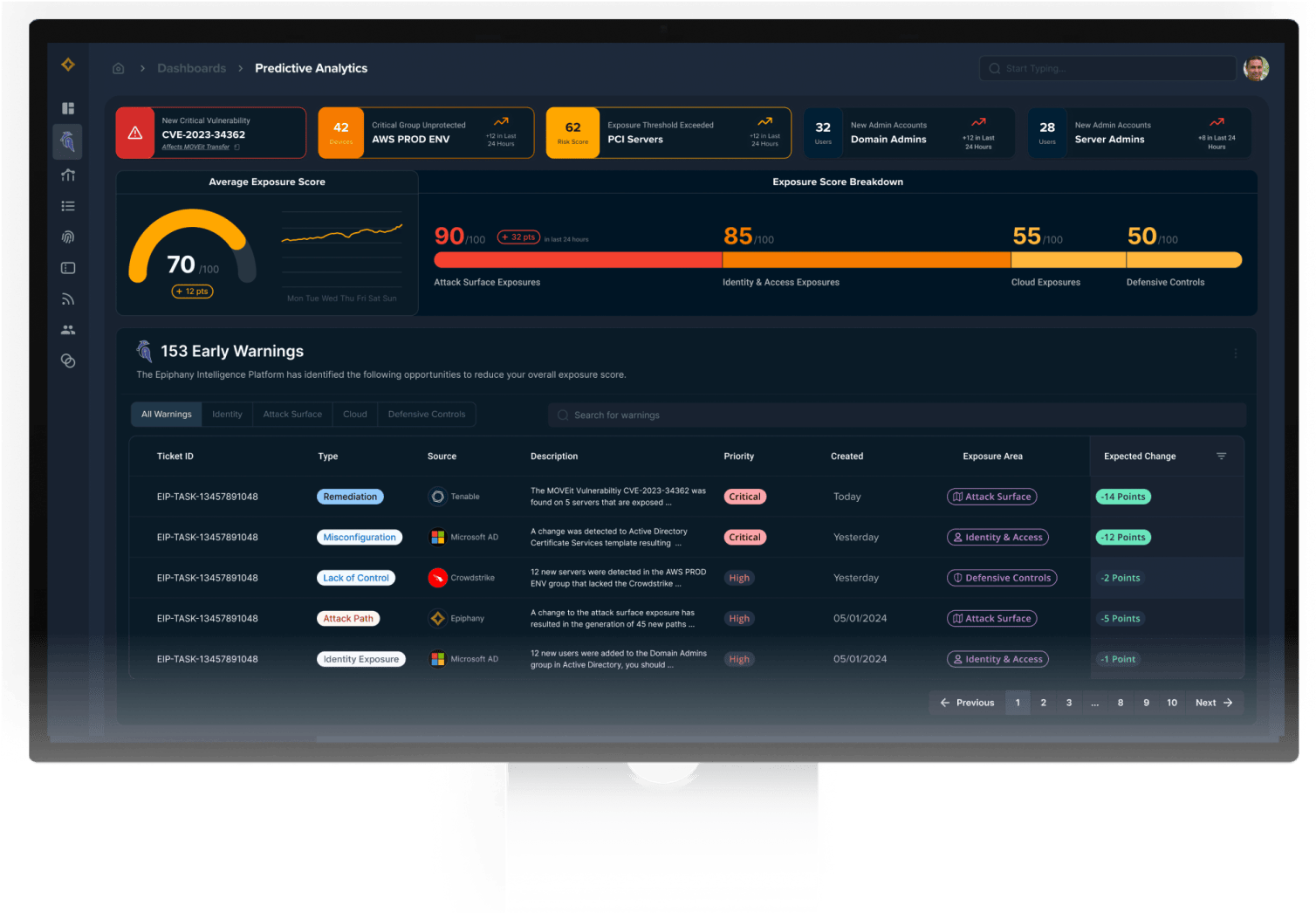
The Epiphany Intelligence Platform combines unparalleled visibility with a knowledge of real-time threats.
Epiphany’s A.I. – guided by our expertise within the 24/7 Reveald Fusion Center – continuously analyzes the environment to generate early warning signs of attack.
We’re giving teams a way to make the biggest possible impact with limited resources and effort – arriving Fall 2024.
Master the attacker’s perspective to reduce business risk.
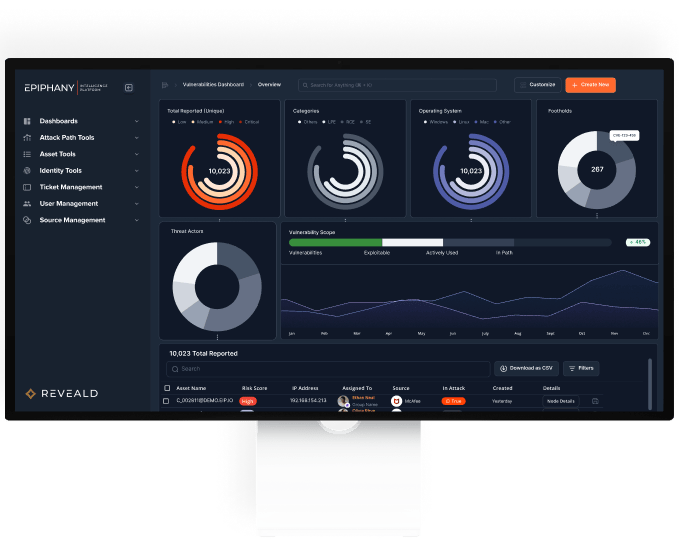
Designed for enterprise and service providers, Epiphany creates a force-multiplier for cyber risk reduction.
Using the power of AI against a configuration and exploit digital-twin of your network, Epiphany finds every possible attack path to your precious assets, and every chokepoint attackers leverage to get to them.
Epiphany uses identity, misconfiguration, and vulnerability problems to find the ways an attacker could traverse your network and compromise your security, and provides you with a prioritized list of the most important changes to make to radically block those attacks.

"The objective of CTEM is to get a consistent, actionable security posture remediation and improvement plan that business executives can understand and architecture teams can act upon."
Continuous Threat Exposure Management (CTEM) refers to a series of processes that enable enterprises to continuously and consistently assess the visibility, accessibility, and vulnerability of their digital assets. In the past, companies focused solely on vulnerability management, which did not adequately address the problem of effectively reducing material risk.
By incorporating business impact analysis and understanding how vulnerabilities, misconfigurations, and attack strategies can intersect, CTEM offers a more comprehensive approach to mitigating risks.
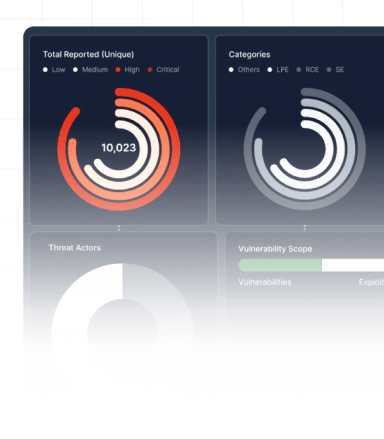
The Epiphany Intelligence Platform is a comprehensive solution to assess material risks to your digital environment and business operations.




Welcome to the new age of predictive cybersecurity.
Leverage the power of AI to discover and prioritize cybersecurity risks, vulnerabilities and misconfigurations across your entire environment
