
Use Case: Incident Response
Recovery & Preparation
Support the SecOps manager to reduce the time and effort to investigate cyber security incidents.

Support the SecOps manager to reduce the time and effort to investigate cyber security incidents.
Cyber incident response, recovery, and preparation are crucial aspects of cybersecurity that enable organizations to effectively handle cyberattacks, minimize their impact, and restore normal operations quickly. These processes play a pivotal role in safeguarding sensitive data, protecting an organization's reputation, and maintaining business continuity.
Cyber incident response focuses on the immediate actions taken to identify, contain, eradicate, and recover from a cyberattack. It involves a coordinated effort from various teams within an organization, including IT security, legal, and communications. Effective incident response aims to:
Cyber incident recovery encompasses the steps taken to restore normal operations and fully recover from a cyberattack. It involves:
Cyber incident preparation involves establishing comprehensive plans and procedures to effectively handle cyberattacks. This preparation includes:
Cyber incident response recovery and preparation are indispensable elements of a robust cybersecurity strategy. By effectively preparing for, responding to, and recovering from cyberattacks, organizations can minimize their risk, protect their valuable assets, maintain business continuity, and safeguard their reputation in the face of evolving cyber threats.
Identify potentially exploited vulnerabilities that allow initial access and internal lateral movements.
Epiphany discovers attack paths that could lead to the compromise of business-critical assets and identifies the opportunities for lateral movement and movement between vulnerabilities, identity compromise, and control failures.
By having access to an exhaustive catalog of attack paths and the common intersections, businesses can proactively protect themselves and act to contain potential threats.
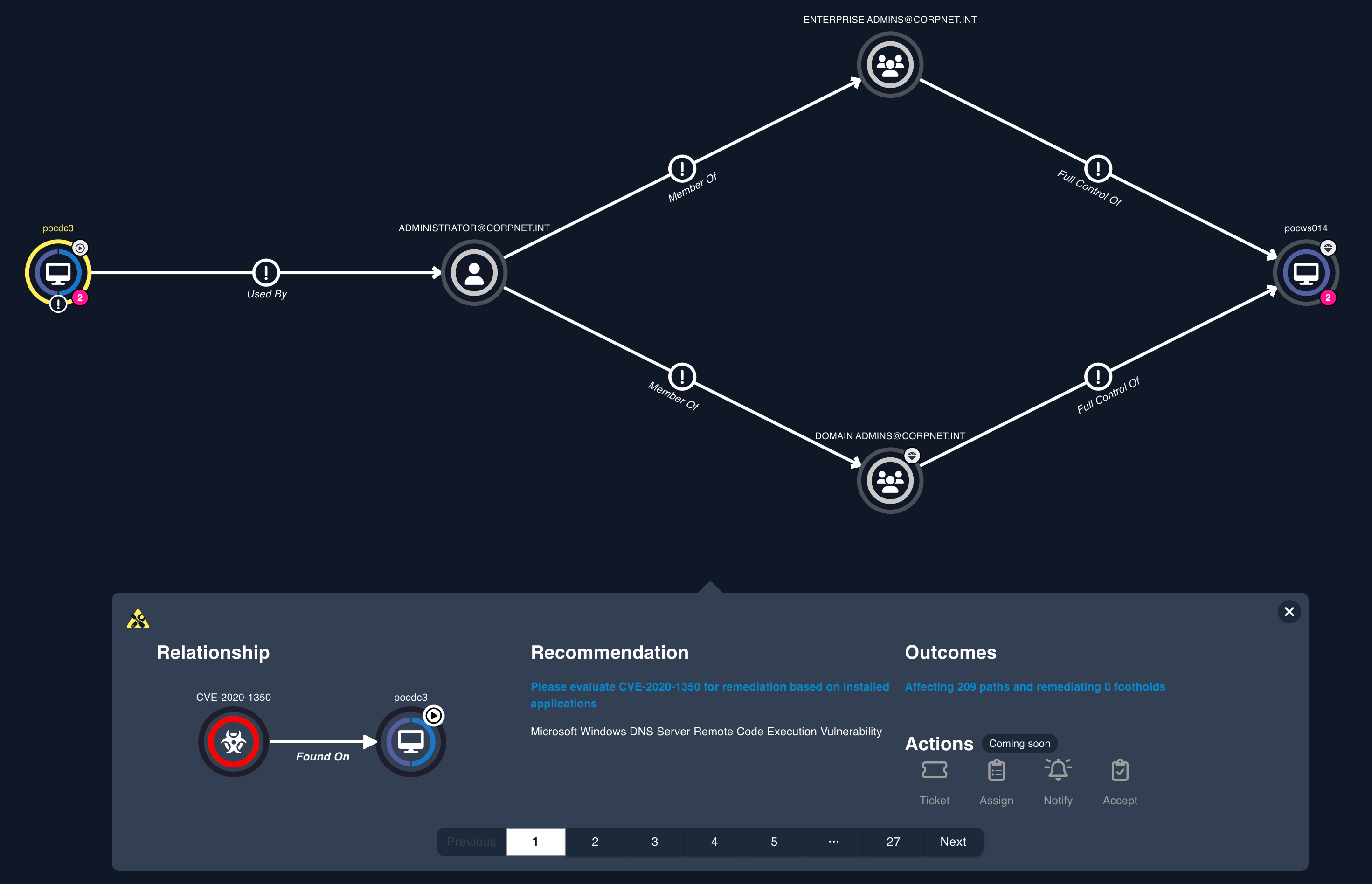
Attack Path
Enable understanding of the attacker’s path to enhance incident response measures.
Epiphany provides context of both how issues could be used to gain access to business-critical systems, and recommendations as to how to mitigate, monitor and contain such. By prioritizing remediation of the attack-path informed actions, material business risk can be reduced.
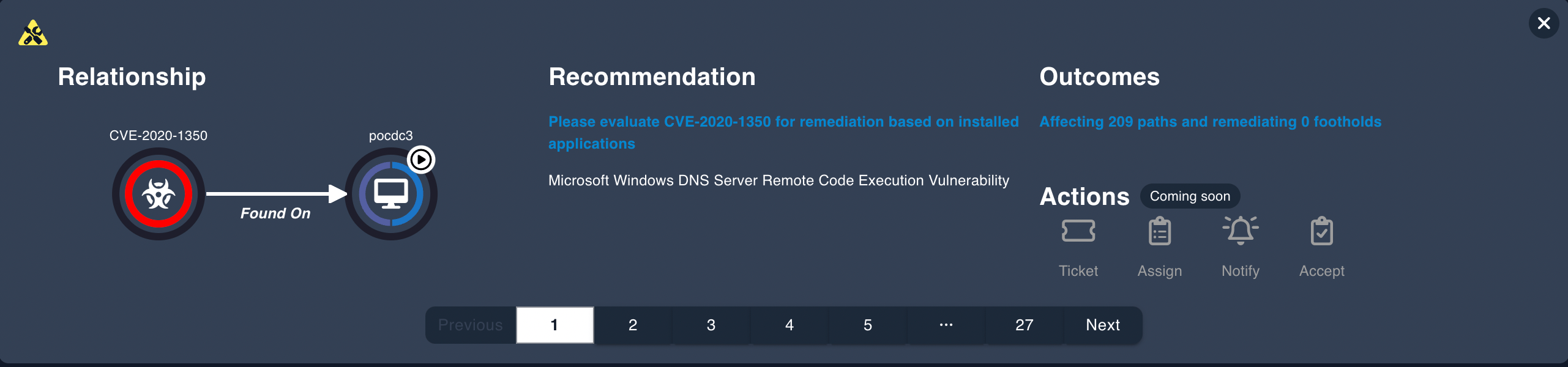
Attack Path Recomendation
Reveald combines decades of cybersecurity experience with leading technology and techiques, allowing customers to shift to predictive security instead of chasing ghosts.