Vulnerability Management Team
Vulnerability management and prioritization are essential components of a robust cybersecurity strategy. By proactively identifying, assessing, and addressing vulnerabilities in their IT systems, organizations can significantly reduce their cyber risk, protect valuable assets and sensitive data, maintain compliance with industry regulations, and optimize resource allocation.
Effective vulnerability management involves continuous monitoring and evaluation of IT systems to detect and prioritize vulnerabilities based on their potential impact. This risk-based approach ensures that organizations are focusing their resources on the most critical threats, maximizing their cybersecurity efforts. By addressing vulnerabilities promptly, organizations can minimize their exposure to cyberattacks, protecting their assets, data, and reputation.
Reduce overall material risk to the organization
Defining a vulnerability management strategy based on material risk to the organization is considered the most effective method to prioritize effort, given that almost all organizations can discover far more vulnerabilities than they have resources and time to mitigate, and that many discovered vulnerabilities are theoretical, have not been weaponized by cybercriminals, or do not create material business risk.
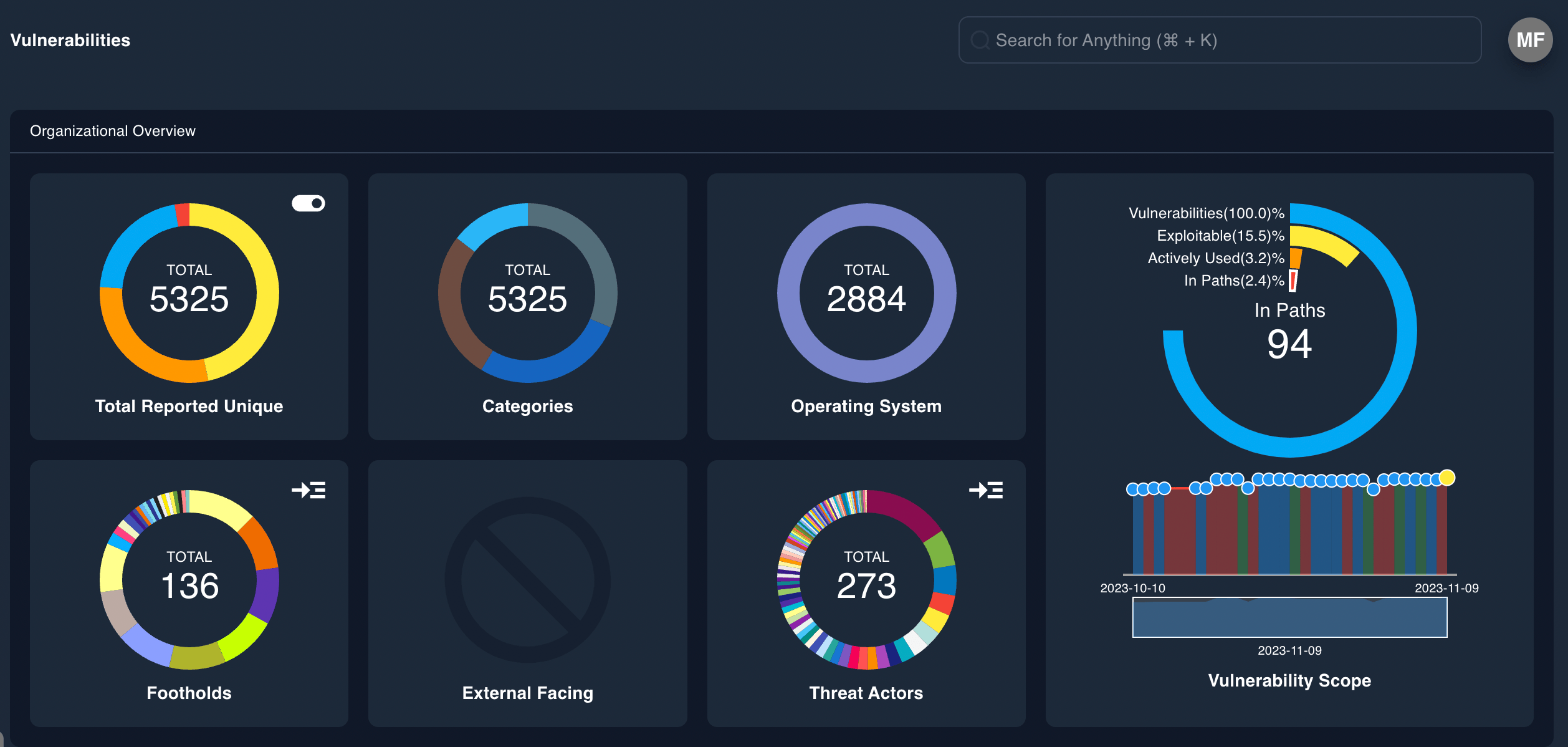
Epiphany correlates vulnerabilities to attack paths to determine which vulnerabilities are:
- Exploitable
- Weaponized
- Lead to an exposure of identified business risk
Vulnerability Management
Risk-Based Prioritization of Vulnerabilities
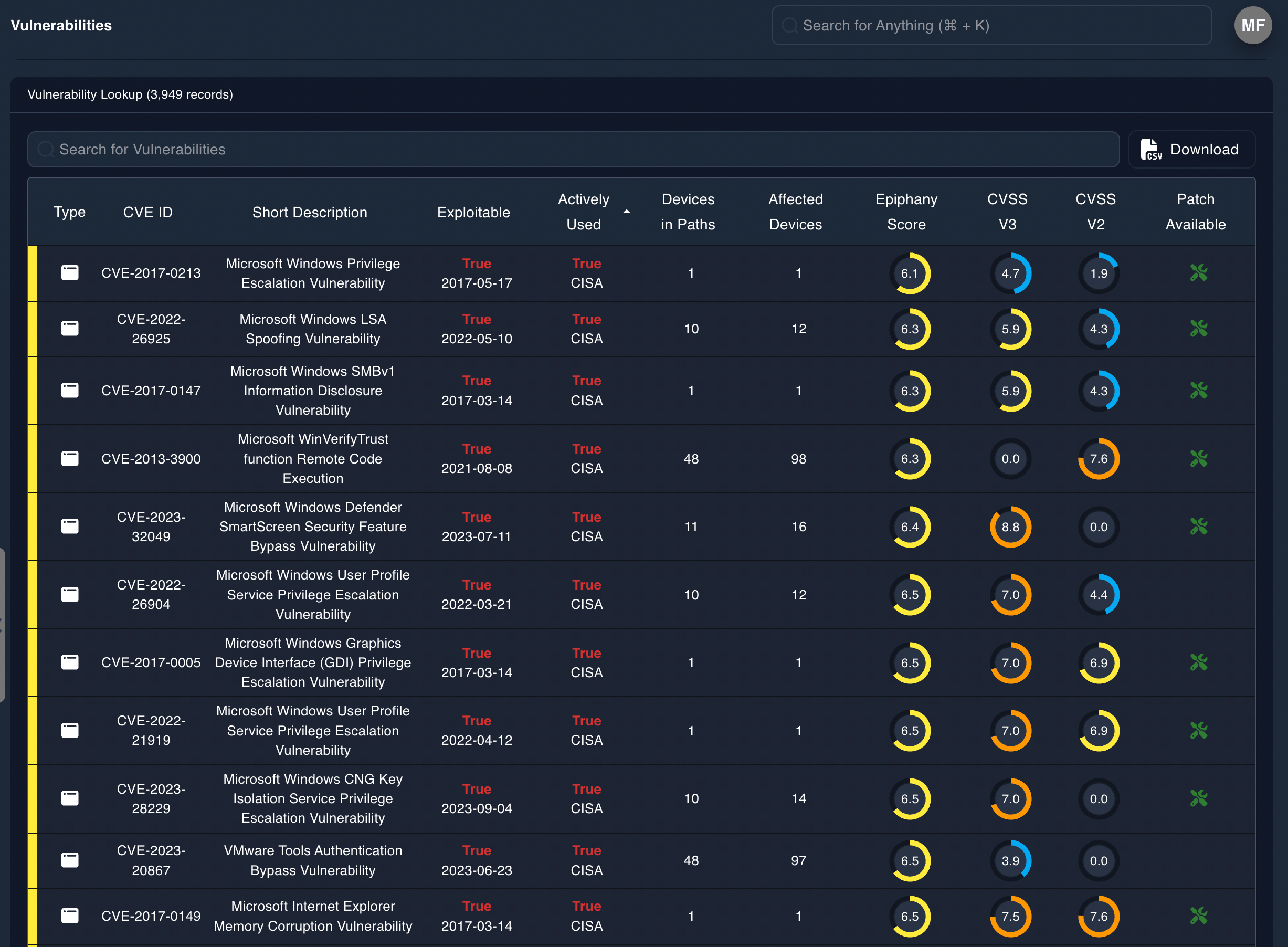
Assume a situation where there are 275 devices containing a total of 12,352 vulnerabilities...
Epiphany—10 seconds
In less than 10 seconds, Epiphany uses AI to analyze its configuration digital-twin to identify 120 vulnerabilities that need to be remediated.
Manual Investigation—4,300 hours
A vulnerability analyst would have to analyze all 12,352 vulnerabilities in existence. This could take over 4,300 hours of time, based on average analysis time of 21 minutes.
Reduce operational workload over traditional vulnerability management methods and approaches
Using Epiphany, Reveald reduces reconnaissance, identification, investigation, and remediation time and effort by applying Continuous Threat Exposure Management (CTEM) practices.
The CTEM approach continuously monitors and assesses the security posture of an organization. This allows for the identification and remediation of vulnerabilities before they can be exploited by attackers. CTEM also provides organizations with more comprehensive visibility into their attack surface, enabling them to prioritize remediation efforts and make more informed security decisions.
Epiphany reduces an insurmountable program of work and turns it into a set of achievable and actionable outcomes.
Additional information from the NIST Cybersecurity framework (CSF):



