
Cybersecurity Posture Measurement
For A Global Conglomerate
Using Malware validation to ensure cybersecurity posture

Using Malware validation to ensure cybersecurity posture
Our customer ranks as the 6th largest privately held company in the United States, boasting annual sales exceeding $40 billion USD. With operations spanning 18 countries across North, Central, and South America, Europe, the Middle East, and Asia Pacific, the company operates on a global scale with significant exposure to cybersecurity threats.
Given the magnitude of their operations and the diverse geopolitical landscape they operate in, the customer faces an ever-evolving array of cyber threats. They recognize the critical need to validate the components of their cybersecurity posture rigorously. This includes ensuring the effectiveness of defense protocols, incident response plans, proof-of-concept implementations, and fine-tuning of cybersecurity technologies.
Our technology provides a comprehensive suite of solutions tailored to address the customer's cybersecurity challenges. The initial use cases identified include:
EVE leverages cutting-edge technology to offer dynamic and comprehensive testing scenarios that mimic actual cyber threats
By integrating EVE into your security strategy, you ensure that your organization is not just reacting to threats, but proactively preparing for them.
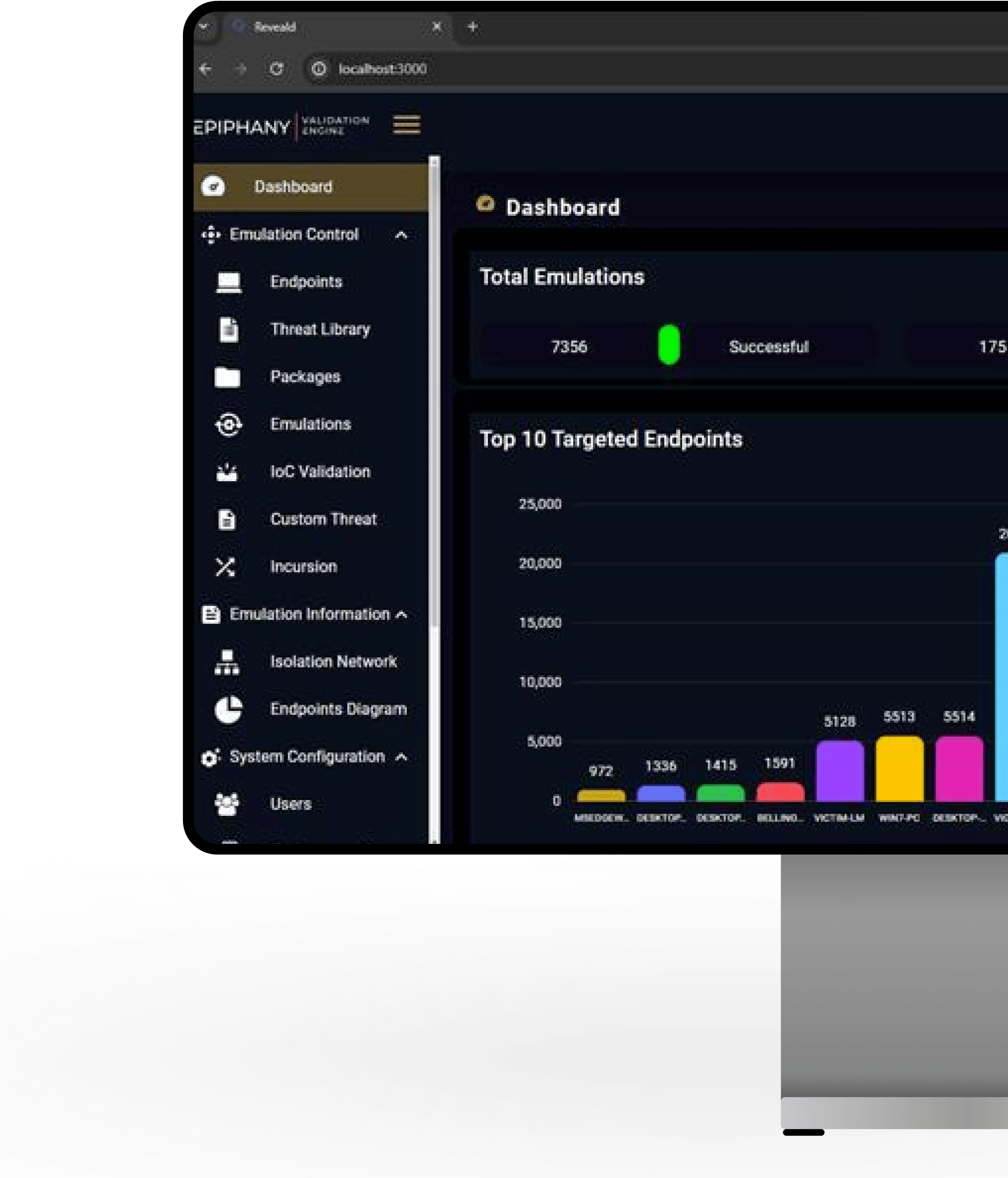
Our evaluation among other vendors highlighted our exceptional performance in crucial areas:
The customer is thrilled with the results achieved through our technology and plans to continue collaborating with us to further enhance their cybersecurity posture. As their trusted partner, we are committed to evolving our product to meet their evolving needs and navigate the ever-changing cybersecurity landscape effectively. Together, we are ensuring that the customer remains resilient against cyber threats and maintains their position as a global leader in their industry.
Contact Us